Security Reporting
The use of Infrastructure as a Service (IaaS) presents many challenges in regards to security. Most importantly, it requires rethinking how applications and infrastructure are secured and audited. The perspective on how to do this needs to be rethought and security teams need to build new processes and procedures to accomplish tasks such as perimeter assessments, penetration tests, vulnerability assessments, user-rights reviews, and security audits. CloudCheckr was designed to address this new paradigm and helps with many of the new security requirements for the public cloud. CloudCheckr provides more than 500 security checks for AWS. Out of the box, CloudCheckr will perform an assessment of the security settings and save that into its Best Practices results. CloudCheckr offers reports and alerting on AWS CloudTrail and Config data, in-depth VPC and security group analysis, and perimeter assessments. Using CloudCheckr, the security team can review security for an entire AWS environment on daily basis.
Best Practice Checks
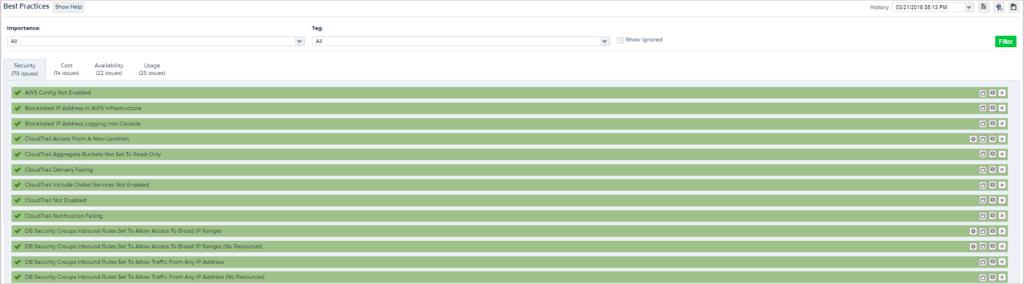
CloudCheckr's Best Practice Checks alert you to any potential issues within your AWS deployment. The checks include looking at your security group and network ACL rules, ensuring your root user isn't accessing your account, finding publicly-accessible resources, and ensuring you have proper IAM policies in place. The checks also ensure that you have enabled and properly configured AWS security features like CloudTrail. Review the topic, Best Practice Report, for more information.
CloudTrail
CloudTrail is an AWS service that records any interaction with your AWS account and logs those interactions within a user-defined S3 bucket. The log information includes the timestamp, source IP address, IAM identity, request and response parameters, and resources, if applicable. CloudCheckr offers several reports around CloudTrail including summary reporting, a list of trails so you can monitor the configuration and health of your CloudTrail log delivery, events reporting where you can search, filter, and group your log event history, and alerting so you can be notified when critical events occur within your AWS account. Review the topic, Cloudtrail Report, for more information.
AWS Config
AWS Config provides resource inventory, configuration history, and configuration change details to AWS customers. AWS Config allows you to take snapshots of your AWS deployment, so you can see exactly how each resource was configured at any point in time. These capabilities enable compliance auditing, security analysis, resource change tracking, and troubleshooting. CloudCheckr takes this config data and allows you to search and filter by resources and configuration changes. You can preform side-by-side comparisons to see exactly what has been modified at the resource level. You can also load any of your configuration snapshots into CloudCheckr, where they are fully searchable. Review the topic, AWS Config Reports, for more information.
VPC
Amazon VPC lets you provision a logically-isolated section of the Amazon Web Services (AWS) cloud where you can launch AWS resources in a virtual network that you define. You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways. CloudCheckr provides several important reports to give you visibility and control over your VPCs, their traffic, and the resources residing within those VPCs. You can see a full inventory of each of your VPCs, including their route tables, network ACLs, internet gateways, subnets, resources, etc. The Traffic Analysis report will show you exactly how traffic flows in, and through, your VPCs. There are also summary and details reports for your subnets and network ACLs. Review the topic, VPC Reports, for more information.
Security Groups
Security groups act as a virtual firewall that controls the traffic for some AWS resources. Security groups contain Inbound and Outbound rules that dictate who and what is able to connect to the resources. CloudCheckr provides a summary and details report for security groups across several services. These reports provide important details about each of your security groups, including their Inbound and Outbound rules, and which resources the security groups are associated with. Review the topic, Security Groups, for more information.
Perimeter Assessment
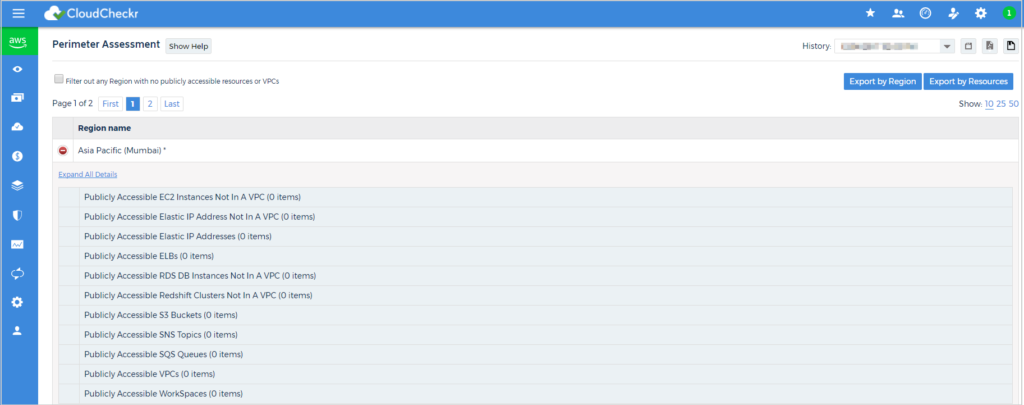
The Perimeter Assessment report shows you an analysis of all the entry points from the public internet into your AWS account. Reviewing the public entry points allows you to determine if you've unintentionally left any openings in your AWS environment that expose you to the public internet. The report will provide you with a list of your publicly-accessible resources both within, and outside of VPCs, grouped by region. When expanding on the resources within the report, you'll also see the rule(s) that are making the resources publicly accessible.
Change Monitoring
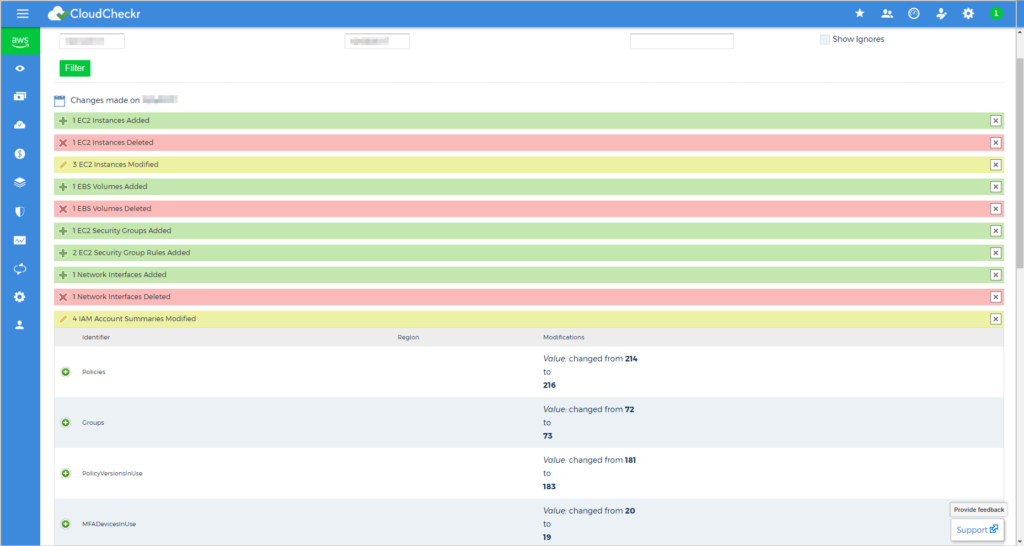
Each day CloudCheckr takes an inventory of your AWS deployment and compares that against the previous day. Any resources that have been added, deleted, or modified will be included in this report. Review the topic, Change Monitoring, for more information.
Permissions
The Security Permissions Report shows you a comprehensive set of permissions and policies against your S3 buckets and EC2 instances. For your EC2 instances, the report will list the security groups, instances, network ACL rules, and IAM policies that are associated with the resource. For S3 buckets, you'll see all access control lists, bucket policy permissions, and IAM policies that allow access to the buckets.
S3 Encryption
The S3 Encryption report shows results of a security sweep of available S3 buckets seen from this account. Following the scan, the total number and list the unencrypted object . The report also indicates the date and time (UTC) of the last successful security scan. The report will not display the object name of any encrypted object or any other identifiable characteristic(s).
