Aggregate CloudTrail Collection in CloudCheckr
Aggregate CloudTrail enables security administrators to report on and audit all the CloudTrail data in a deployment while providing account owners access and control over their CloudTrail data. With Aggregate CloudTrail, security administrators can see, identify, and search for any CloudTrail event in any log in any account.
This topic will show you how to use a Multi-Account View (MAV) to aggregate your CloudTrail log files from multiple AWS accounts into a single S3 bucket, so you can view the log details and events.
Access to CloudTrail Data
As a security administrator, you can access every CloudTrail event when you set up aggregate CloudTrail for all the AWS accounts in your deployment. With this access, you could find yourself potentially sifting through a lot of data.
But with CloudCheckr's CloudTrail reports, you can search, filter, audit, and conduct forensics on any CloudTrail actions. You can also configure built-in or custom CloudTrail alerts—allowing CloudCheckr to notify you about any events, such as Security Group changes or Unauthorized Access attempts, which may be potentially harmful.
For data protection purposes, account owners can only create alerts in their accounts. However, CloudCheckr account owners and security administrators can view any alert in the deployment—no matter who creates it.
Prerequisites
Before you can configure the Aggregated S3 bucket, you must complete the following actions:
Follow these steps to create an IAM user policy that contains the correct permissions which will allow AWS to access your CloudTrail S3 bucket:
- Log in to the AWS Management Console.
- Scroll down to the Security, Identity & Compliance section and select IAM.
- From the IAM dashboard, click Policies.
- Click Create policy.
The Create Policy page opens.
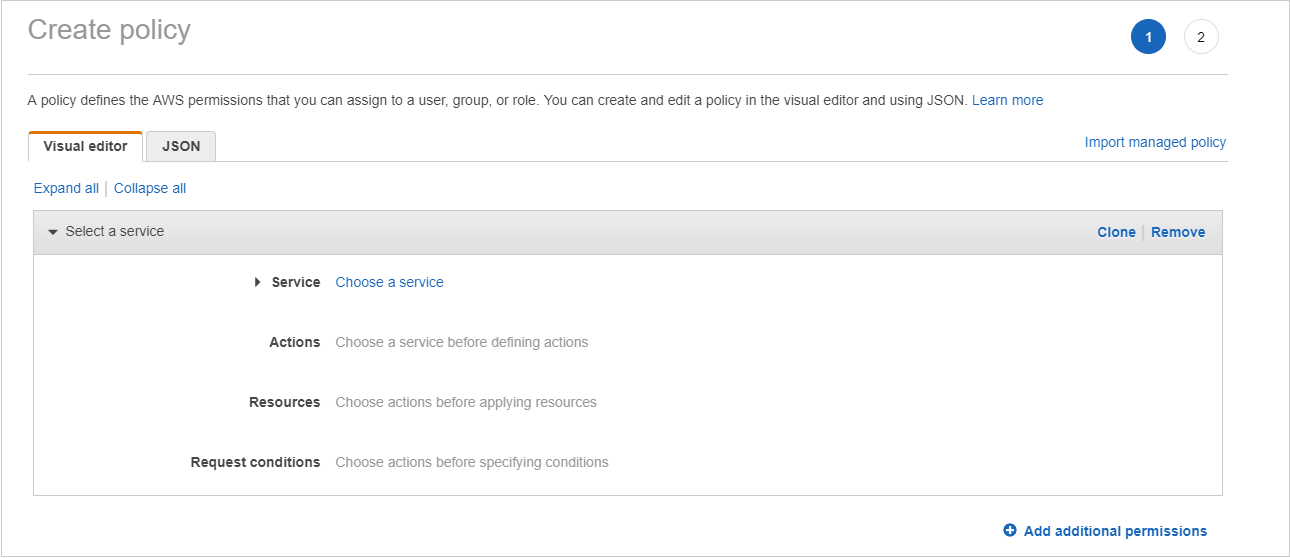
- Click the JSON tab.
- Replace the text in the JSON tab with the following policy:
{
"Version":"2012-10-17",
"Statement":[
{
"Sid":"CloudTrailPermissions",
"Effect":"Allow",
"Action":[
"s3:GetBucketACL",
"s3:GetBucketLocation",
"s3:GetBucketLogging",
"s3:GetBucketPolicy",
"s3:GetBucketTagging",
"s3:GetBucketWebsite",
"s3:GetBucketNotification",
"s3:GetLifecycleConfiguration",
"s3:GetObject",
"s3:ListBucket"
],
"Resource":[
"arn:aws:s3:::[YOUR CLOUDTRAIL BUCKET]",
"arn:aws:s3:::[YOUR CLOUDTRAIL BUCKET]/*"
]
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "*"
}
]
}
- Click Review policy.
- Type a name for the policy and click Create policy.
- Return to the IAM dashboard and click Users.
- Click the Add user button.
- On the Add user screen:
- Type the username for the new IAM user.
- Select the Programmatic access check box to generate an access key and secret key ID.
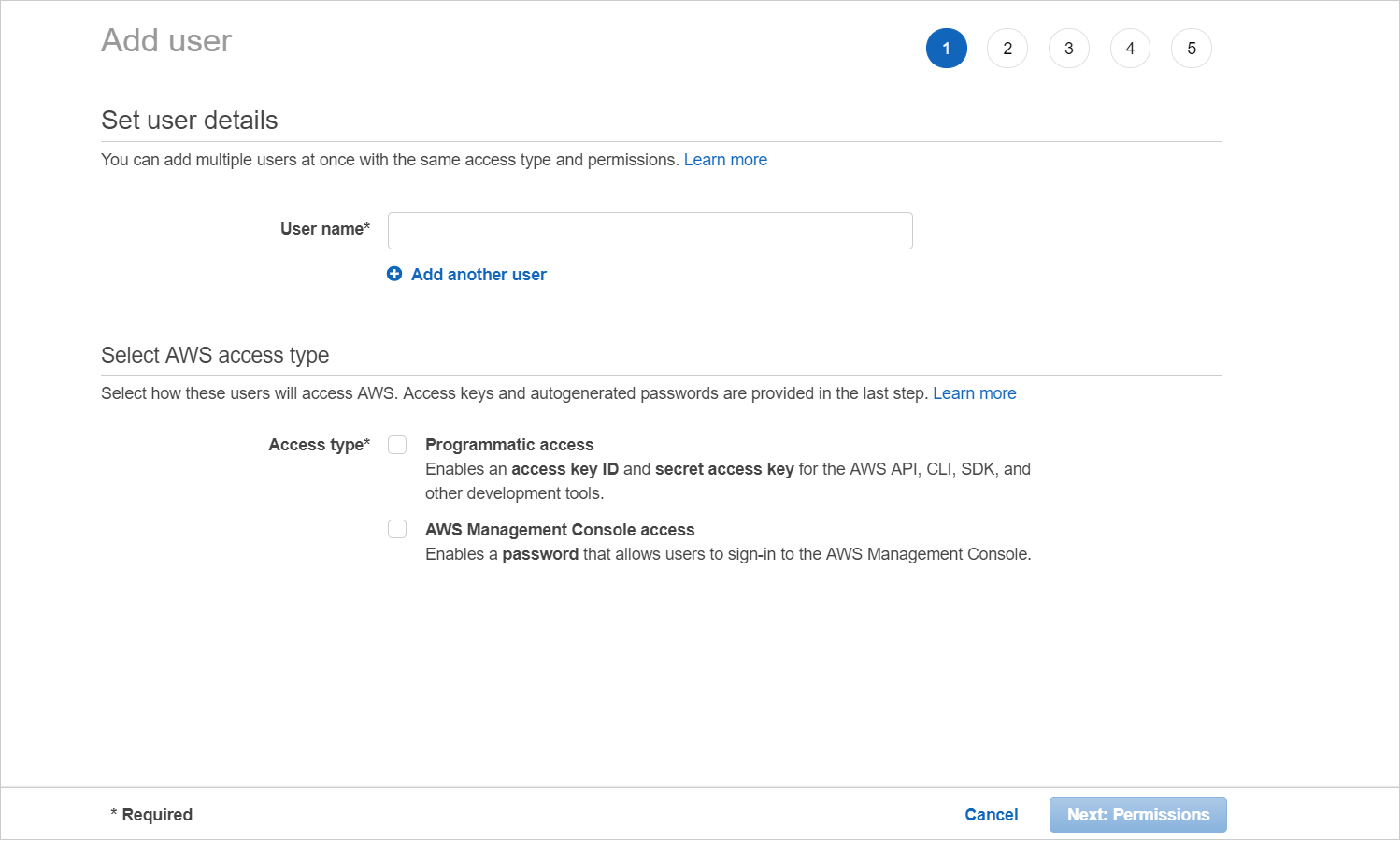
- Click Next: Permissions.
- Click Attach existing policies directly.
- Select the IAM user policy you created and click Next: Tags.
- Click Next: Review.
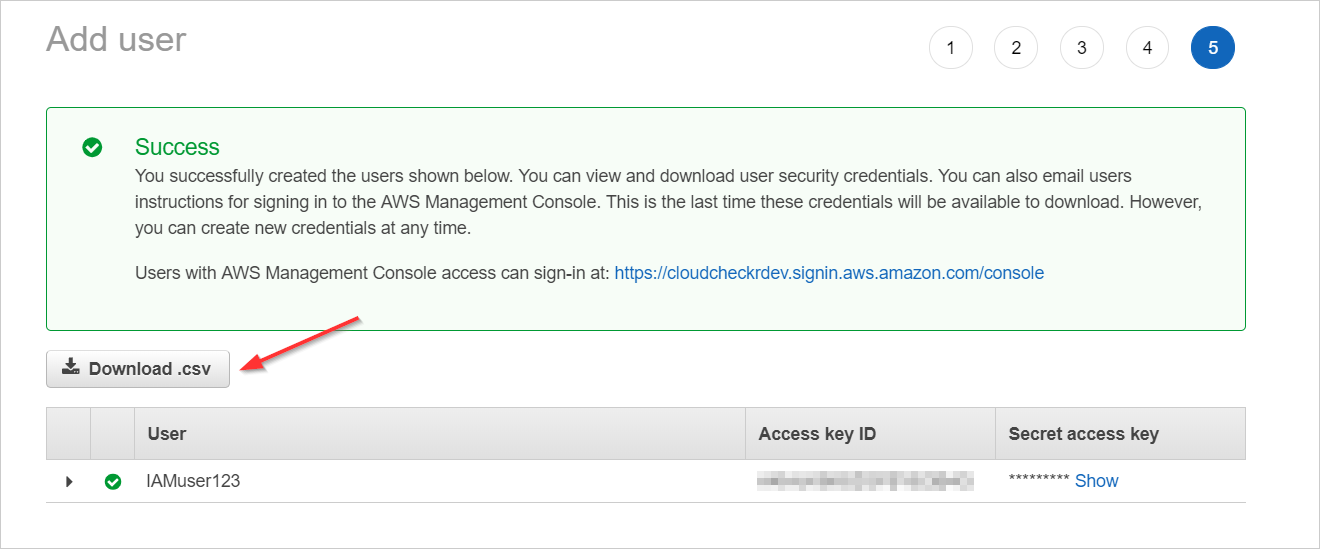
- Review your choices and click Create user.
- Click Download .csv to save the access and secret access keys as a .CSV export and click Close.
Procedure
- Launch CloudCheckr.
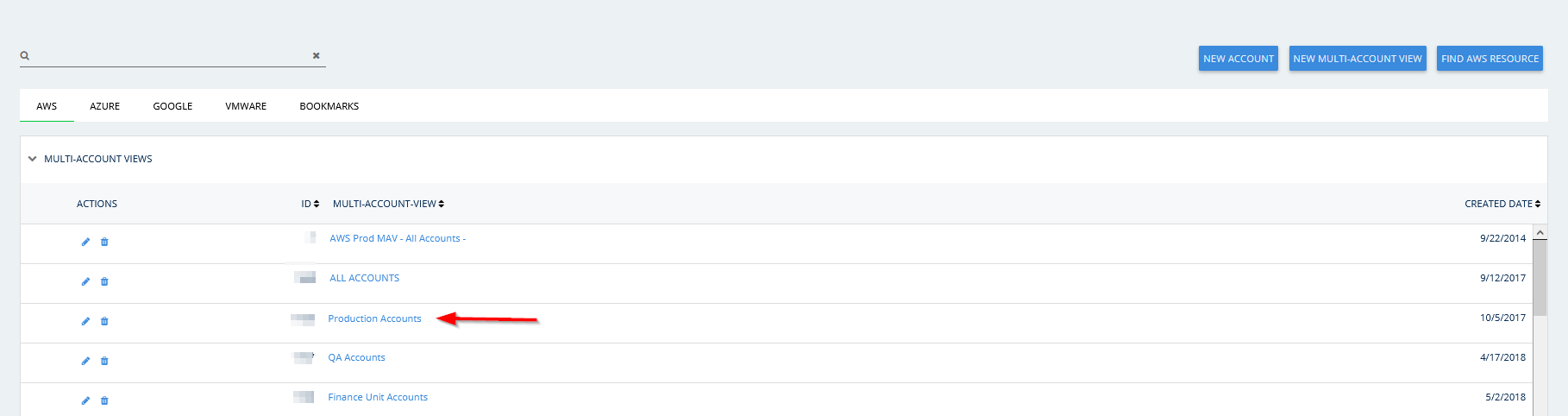
- Select a MAV from the list of MAVs on the Projects page or create a MAV.
For the purposes of this procedure, we selected the Production Accounts MAV.
- From the left navigation pane, choose Security > Activity Monitoring > AWS API (CloudTrail) > Aggregated S3 Buckets > Configure.
The Configure Aggregated S3 Buckets page opens.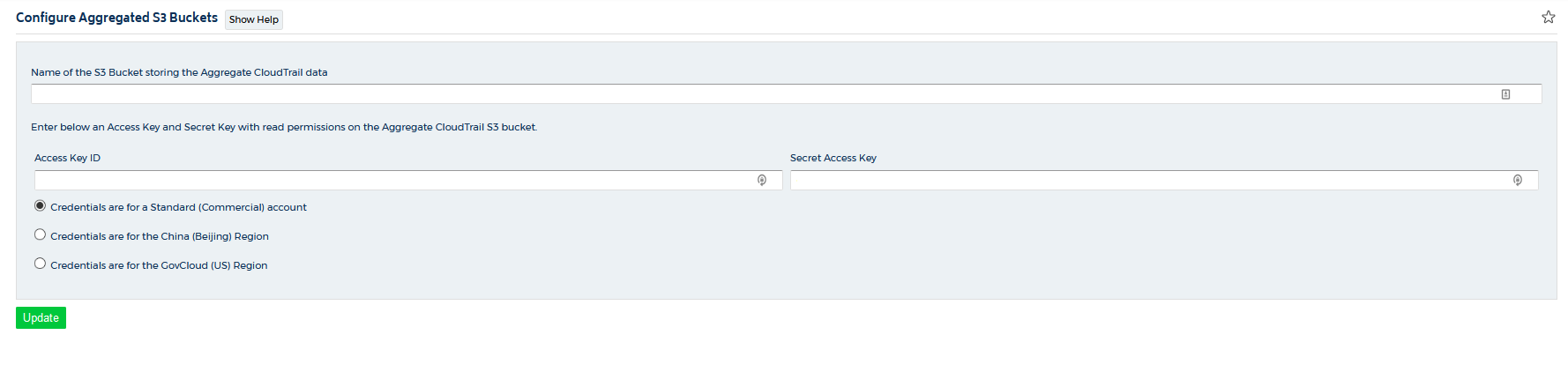
- In the Name of the S3 Bucket storing the Aggregate CloudTrail text field, type the name of the S3 bucket where you are storing your aggregate CloudTrail log files.
- Copy the access and secret keys located in the CSV export file you created in the Prerequisites.
The IAM user must exist in the same AWS account as the S3 aggregated bucket.CloudCheckr recommends restricting the s3:GetObject permission to only the s3 bucket with CloudTrail data.
- Click Update.
CloudCheckr will now begin to download the CloudTrail data from that S3 bucket. Once it's complete, you can use the CloudTrail events report in this MAV to explore the CloudTrail data.
