Setting Up Aggregate AWS Config Collection in CloudCheckr
AWS allows you to combine AWS Config log files from multiple AWS accounts into a single S3 bucket using CloudCheckr's Multi-Account View (MAV). In a MAV, you can view the details and changes from these config logs. CloudCheckr will also automatically filter the data from the MAV into standard accounts
Procedure
- Load or create the MAV you want to configure from your list of MAVs.
- From the left navigation pane, choose Security > Activity Monitoring > Resources (AWS Config) > Aggregated S3 Buckets > Configure.
The Edit AWS Aggregated AWS Config Credentials And Buckets page opens.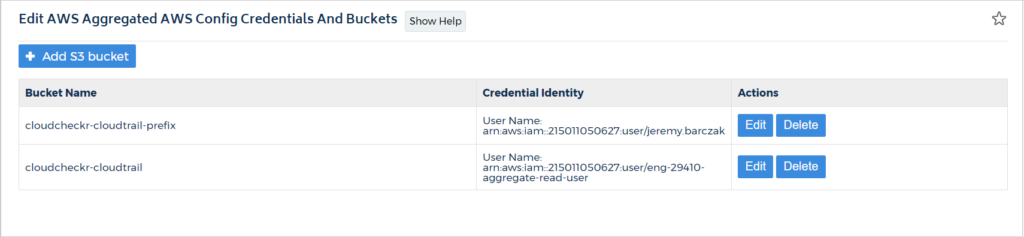
- Click + Add S3 bucket.
The New Cloud Aggregate Credential dialog box opens.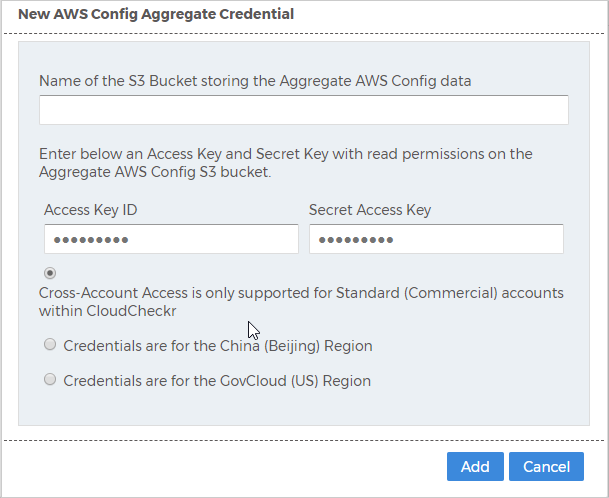
- In the Name of the S3 Bucket storing the Aggregate AWS Config data field, type the name of the S3 bucket where you are storing your aggregate AWS Config logs.
- Type the access key and secret key of the IAM user who has permissions to access the S3 bucket that contains the aggregate AWS Config logs and click Add.
The IAM user must exist in the same AWS account as the S3 aggregated bucket.Review Creating Credentials Using an IAM Access Keys for instructions on how to create an IAM access key and secret key.
- Click IAM User Policy to view and copy the permissions you need to access the Aggregate AWS Config.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"s3:ListAllMyBuckets",
"s3:List*"
],
"Effect": "Allow",
"Resource": "*"
},
{
"Action": [
"s3:GetObject",
"s3:GetBucketLocation"
],
"Effect": "Allow",
"Resource": [
"arn:aws:s3:::NAME-OF-CONFIG-BUCKET*",
"arn:aws:s3:::NAME-OF-CONFIG-BUCKET/*",
"arn:aws:s3:::NAME-OF-CONFIG-BUCKET"
]
},
{
"Action": [
"iam:GetUser"
],
"Effect": "Allow",
"Resource": "*"
}
]
}CloudCheckr recommends restricting theCloudCheckr will now begin downloading the data from that AWS Config bucket. Once complete, you can use the AWS Config reports within MAV to explore the data.s3:GetObjectpermission to only the s3 bucket that contains the AWS Config data.
